
Information transformation
Reduce risk and ensure security and compliance for the information you hold
Business objective: Data, IT security and resilience
Contact usRedefine how you safeguard your most critical asset
Have you ever considered what could happen if your organisation's most valuable assets were compromised? In today’s digital landscape, protecting your reputation is more crucial than ever. Yet, many organisations grapple with internal and external risk factors—ranging from data loss and misuse to cyber attacks and IT asset mismanagement. What if there was a way to stay ahead of these threats, ensuring your assets remain secure and your reputation intact?
At Iron Mountain, we’ve earned the trust of over 240,000 organisations worldwide, including more than 90% of the Fortune 1000. We make it effortless for you to stay abreast of the latest protocols, ensuring your asset and information management is not just compliant, but proactively secure.
Curious about how we can help you mitigate risk and safeguard your most critical assets?
Over 90%
of the Fortune 1000 trust us
with their data
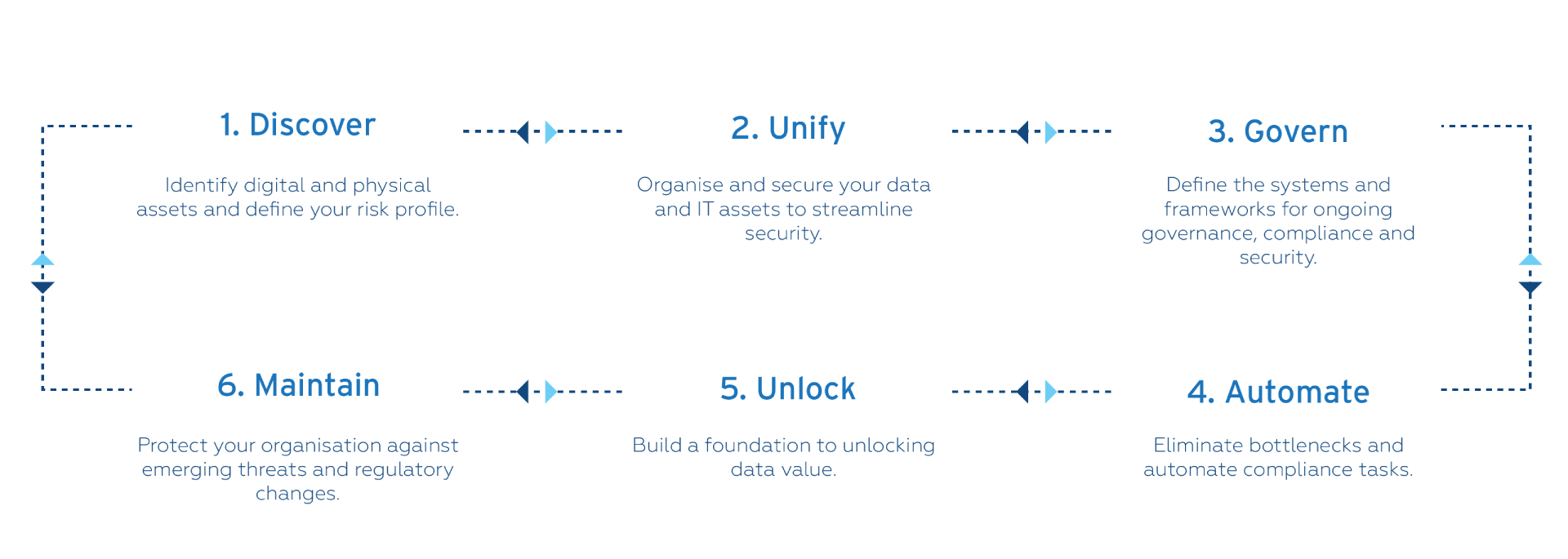
How do we do it?
Through our information transformation framework we help your organisation improve security, innovation and resilience
Click on each phase to jump to the respective part of this page.
Understand how to prevent a breach in your organisation
Explore our scanning, digital storage and governance solutions
Reduce risk and increase resilience with workflow automation
InSight digital experience platform
Access information from a unified, automated, secure platform
Smart Sort
Efficiently unmingle your commingled files—all without a complex, labour-intensive discovery project
Digital Mail
Digital Mail is as easy to set up as it is to use. Our complete end-to-end solution handles everything from mail pickup to disposition, all with an auditable chain of custody.
Ensure your data, information and IT assets remain compliant and protected:
Learn more about how to undergo an information transformation
Take the next step. Click below to learn more:
By transitioning from physical to digital with a unified asset framework, structured records and data, your digitised information and data can unlock valuable insights through automation.
Build a strong and flexible information framework to drive security, innovation and resilience for your organisation.
Given the changing nature of the hybrid workforce, redeploy and retire costly real estate with digitised assets, and free your people from manual tasks with automation.
Explore more resources











